How To Identify Spam Email
Spam Email Identification
Despite the commonality of phishing attacks (email-based), more than 80% of businesses fall for these deceptive tactics. Some emails look so authentic and compelling that it is easy to fall prey to the bait. And once you, a fish, get into the hacker’s net, your data and identity can be compromised in no time.
Ways to Identify Spam Emails
Phishing is a sophisticated cyberattack of netting users via email to obtain confidential information for ill purposes. These emails can 99% look like ones from your contacts. But the following distinguishes a bad email from a genuine one:
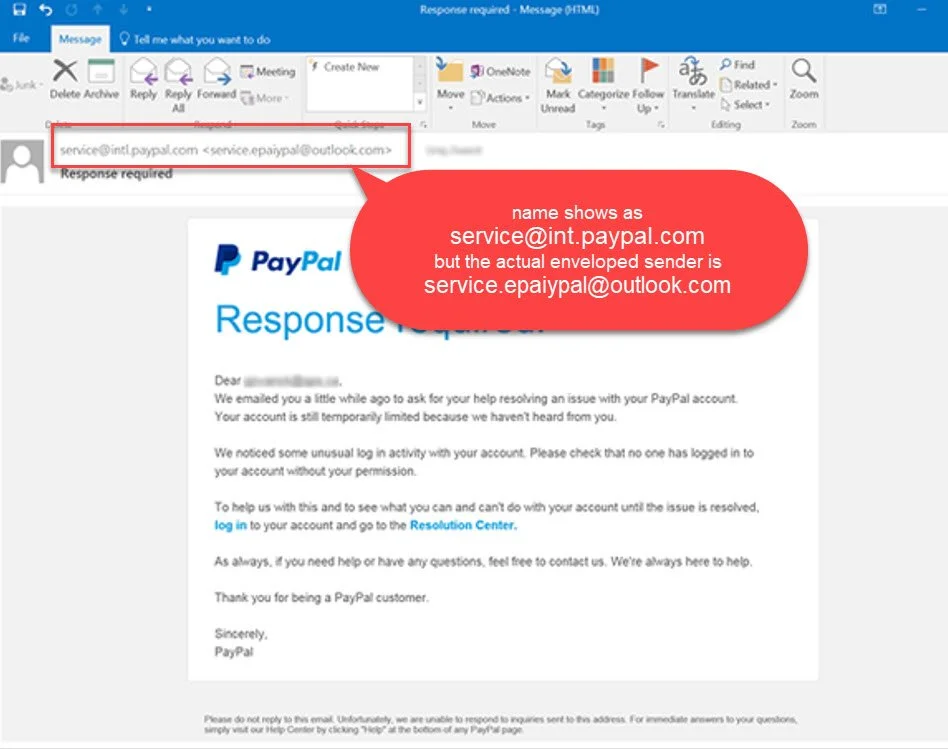
Suspicious Email Domain
Usually, a phishing email comes from a public domain, not a company-specific domain. This is a straightforward way to identify spam, but you can also encounter tricky attacks. So, make a quick Google search to confirm the legitimacy of the business before performing any action. Also watch for Spoofing. Spoofing is when the name shows someone you are familiar with, but the email address is different.
Illegitimate Greetings
Look for unnecessary empathy, that befriending attitude, and greetings you don’t relate with. That “dear friend” salutation or a user you haven’t ever interacted with is a major red flag. On the other hand, phishing email greetings can also be impersonal and generic. Please don’t fall for it.
Skeptical Contents
You can identify spam emails by looking at their content. “Service updates,” “lottery,” “action required,” or “buy now” are words you must watch out for. These can sound unexpected, create a sense of urgency, make you click links or download files, and ask for sensitive information such as your financial details. The content is absurd, and that’s probably a scam.
Protect Yourself Against Phishing Attacks
With time, phishing attacks are also evolving. But some practical measures and user discretion can help you stay safe online.
· Raise awareness within the organization to help employees contain and report the issue.
· Watch out for suspicious links or attachments, and do not provide any data to unverified sources.
· Utilize a secure email filter to block unwanted and fraudulent emails from reaching your server.
· Enable multifactor authentication to prevent scammers from easily accessing employee accounts.
· Remember, legitimate organizations never request confidential details over emails, calls, or texts. If someone does, you’re at risk.
· If your business has fallen for a phishing attack, notify the IT team ASAP – don’t restart or shut your servers or devices.
Ultimately, the last line of defense in phishing attacks is the user. Stay alert, stay aware, and have protocols in place to protect your company and stay safe in the digital world. For more information, get in touch with the CCI team to help you get started on creating indisputable anti-phishing campaigns.