Security News- Android Exploit and MFA Fatigue
Android Lock screen Exploit
A recent security update for Android versions 10, 11, 12, and 13 patches an exploit for Android devices where the Lockscreen of the device could be bypassed.
Researcher David Schütz discovered a widespread exploit for all Android devices where triggering the SIM authentication window and incorrectly entering in the SIM PIN would lock the device. Once locked, switching the SIM card with an alternative SIM would allow the user to reset the PIN, and bypass the lockscreen entirely.
The bug occurs when the conditions for the lockscreen being dismissed are rushed. Once the SIM’s PIN is reset, a dismiss function is called to move to the next layer of security. While the next layer of security is loading (I.E PIN, password, fingerprints), the SIM card puts out an additional command to dismiss and move to the next layer. Unless there is a second security option the SIM bypasses the security layer entirely, unlocking the phone.
David Schütz has been awarded $70,000 by Google’s Android VRP Team for finding and reporting the software bug. Android users are encouraged to download the latest November 2nd update containing the patch to this exploit.
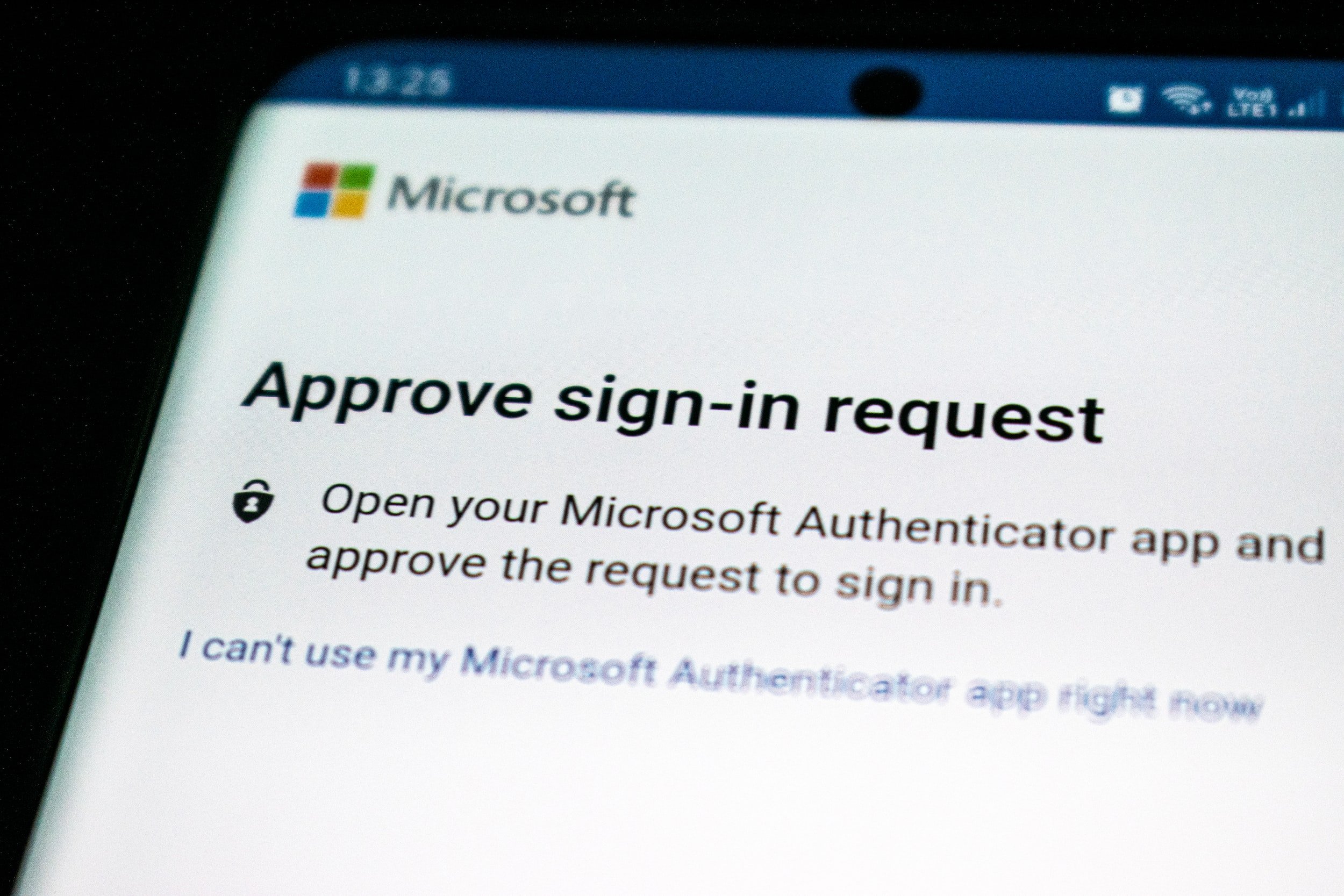
MFA Fatigue: Data Breaching via Social Engineering
As companies enact more stringent measures to protect their data, cybercriminals are beginning to use alternative methods to gain access to networks and employee credentials. The latest tactic enacted tackles the rise of Multi Factor Authentication software, a security method now widely used in the business world.
MFA works by blocking the sign-in of an account until verified by the user, ensuring malicious logins require additional information or access to the device used in authentication. MFA Fatigue is a new data breaching method relying on bombarding the user with continual requests for authentication until they relent, with the actors disguising themselves as IT support requesting the MFA to be accepted.
The tactic relies on pressuring the victim through repeated requests to accept the MFA that can last for hours, as a script automatically sends an attempted user login through the authentication system. Once the victim relents and accepts the MFA prompt, the hackers gain access to the network, allowing them to harvest more data to repeat the process higher up the company chain.
Professionals recommend creating a limit to authentication attempts in a brief time period, and to alert their IT department if continual unauthorized requests are sent to the user after declining access.